 e-Manual e-Manual | Top Site map Site map Help Help Glossary Glossary |
|---|---|
 Category Top
Category Top Overview of the Authentication System
Overview of the Authentication System Setting Administrators
Setting Administrators How User Authentication Works
How User Authentication Works System Requirements
System Requirements Login Methods
Login Methods Setting User Authentication (for the Administrator)
Setting User Authentication (for the Administrator) Managing User Information
Managing User Information Using the Touch Panel Display
Using the Touch Panel Display Using the Remote UI
Using the Remote UI  Registering/Editing User Data for Active Directory Authentication
Registering/Editing User Data for Active Directory Authentication Setting the User Authentication Function Environment
Setting the User Authentication Function Environment Using the Touch Panel Display
Using the Touch Panel Display Using the Remote UI
Using the Remote UI Changing the User Authentication System
Changing the User Authentication System Registering/Editing LDAP Server Information
Registering/Editing LDAP Server Information Users Changing Their Own Passwords
Users Changing Their Own Passwords User Setting Information Management (User Setting Information Management Service)
User Setting Information Management (User Setting Information Management Service) Accessing the Advanced Box of Another Machine
Accessing the Advanced Box of Another Machine Authentication Method Settings for Sending Operations
Authentication Method Settings for Sending Operations Specifying Personal Folders
Specifying Personal Folders Registering Personal Folders for Each User
Registering Personal Folders for Each User Setting Up the Home Folder and Personal Folders
Setting Up the Home Folder and Personal Folders Registering Folders Designated by Login Service as Personal Folders
Registering Folders Designated by Login Service as Personal Folders Specifying Authentication Method for LDAP Server
Specifying Authentication Method for LDAP Server Specifying Authentication Method for Rights Management Server
Specifying Authentication Method for Rights Management Server Specifying Authentication Method for SMTP Server
Specifying Authentication Method for SMTP Server Specifying Authentication Method for File Server
Specifying Authentication Method for File Server Simple Authentication Settings for Secure Print
Simple Authentication Settings for Secure Print Authentication Password Security Settings
Authentication Password Security Settings Displaying a Warning When Logging In with the Default Password
Displaying a Warning When Logging In with the Default Password Allowing the Default Password to Be Used When Logging In from the Remote UI
Allowing the Default Password to Be Used When Logging In from the Remote UI Setting Password Restrictions
Setting Password Restrictions Setting the Lockout Function
Setting the Lockout Function Authentication Settings for Device Information Distribution
Authentication Settings for Device Information Distribution ACCESS MANAGEMENT SYSTEM
ACCESS MANAGEMENT SYSTEM Available Settings for Administrator Table (Touch Panel Display)
Available Settings for Administrator Table (Touch Panel Display) Available Settings for Administrator Table (Remote UI)
Available Settings for Administrator Table (Remote UI) File Formats for Local Device Authentication User Information Files
File Formats for Local Device Authentication User Information Files Other Login Services
Other Login Services Logging In with DepartmentID Authentication (When Department ID Management Is Enabled)
Logging In with DepartmentID Authentication (When Department ID Management Is Enabled) Setting Department ID Management (for the System Manager)
Setting Department ID Management (for the System Manager) Specifying the System Manager Settings
Specifying the System Manager Settings Department ID Management
Department ID Management Using the Touch Panel Display
Using the Touch Panel Display Specifying Department ID Management
Specifying Department ID Management Checking/Printing/Clearing Page Totals
Checking/Printing/Clearing Page Totals Accepting Jobs with Unknown Department IDs
Accepting Jobs with Unknown Department IDs Accepting B&W Copy and Print Jobs without Entering a Department ID
Accepting B&W Copy and Print Jobs without Entering a Department ID Using the Remote UI
Using the Remote UI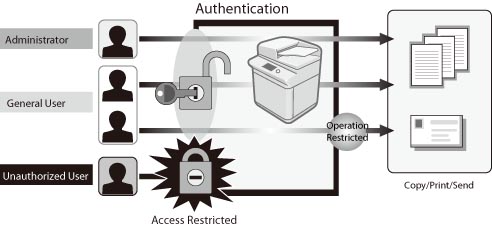
|
User Role
|
Network Related Settings
|
Settings Related to Machine Operations
|
|
Administrator
|
 |
 |
|
NetworkAdmin
|
 |
-
|
|
DeviceAdmin
|
-
|
 |
|
General Users
|
-
|
-
|
|
IMPORTANT
|
|
For details on the ACCESS MANAGEMENT SYSTEM, see "ACCESS MANAGEMENT SYSTEM Administrator Guide."
|