You can increase the network security on the machine to avoid output of data and tampering data and increase the security and confidentiality.
We recommend that you set a Network Administrator (NetworkAdmin) for security reasons when using the SSO-H.
The security on the network for this machine is maintained using the following functions.
SSL Encrypted Communication
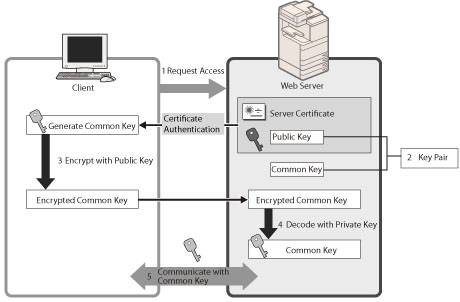
You can perform safe encrypted communication when the user is accessing the machine via a Web browser by installing a server certificate to the machine. With SSL communication, a common key that can only be used by the user and the machine is generated using the server certificate and public key. Doing so will help prevent data interception and theft. See
"Key Pair and Server Certificate Settings for Encrypted SSL Communication" and
"Setting the Key Pair Used With SSL Encrypted Communications."The structure of SSL communication is shown below.
|
1
|
When the user accesses the machine from their computer, the server certificate for SSL and the public key for the server are requested.
|
|
2
|
The certificate and the public key are sent to the user's computer from the machine.
|
|
3
|
Using the public key received from the server, encrypt the uniquely generated common key on the computer.
|
|
4
|
Send the encrypted common key to the machine.
|
|
5
|
Use the private key on the machine and decode the encrypted common key.
|
|
6
|
Now, the user's computer and the machine both possess the common key and can send/receive data using the common key.
|
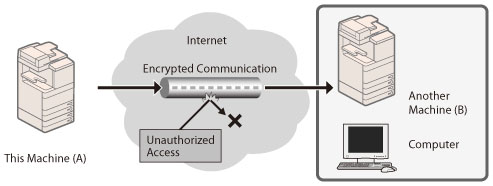
A firewall is a system that prevents access by outside networks, and attacks/intrusions to the network. You can use a firewall on this machine to block access from outside network that appears to be dangerous by restricting communication from specified outside IP addresses.
(See "Protocol Settings.")SNMP is a protocol that manages the entire network. This machine supports SNMPv1 and SNMPv3. SNMP oversees and controls the communication machine connected to this machine via network.
(See "Communication Environment Setup.")IEEE802.1X Authentication
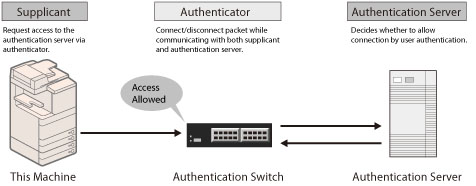
Manages all of the authentication information via the authentication server (RADIUS: Remote Authentication Dial In User Service) and authenticates the supplicant. You can prevent unauthorized access because only the supplicant authenticated by the RADIUS server has permission to connect to the network by the authenticator.
The authenticator blocks communication for the supplicant that is not authenticated by the RADIUS server.
(See "IEEE802.1X Authentication Settings.")IPSec Communication and FIPS 140-2
IPSec is a protocol for creating a security policy to protect data received from and sent to the IP network from threats such as interception, alteration, and theft.
(See "IPSec Settings.")You can also make the encryption method for IPSec communication comply with the United States government-approved FIPS (Federal Information Processing Standards) 140-2.
(See "Using an Encryption Method That Complies with FIPS 140-2.")Advanced Box is a storage location in the machine that stores files in formats, such as PDF, JPEG, and TIFF, which can be used on your computer. There are two types of storage locations in the Advanced Box; Shared Space and Personal Space. In [Advanced Box Settings], you can specify various settings for the Advanced Box such as the Open to Public settings, user authentication settings, and whether to allow users to use the Personal Space.
(See "Specifying the Advanced Box Settings.")In [Network Settings], you can register the Advanced Box of another imageRUNNER ADVANCE series machine which is opened externally with SMB or WebDAV as an external storage location.
(See "Setting the Network.")You can use SSL communication when a MEAP application is used by accessing the machine via a Web browser.
(See "MEAP Settings.")